
September 17th, 2021, Issue #5Service Updates
Phishing Email Simulations
With the rise in ransomware, which commonly uses phishing campaigns to gain unauthorized access to people’s computers, it has become especially important that we all become experts at accurately identifying phishing attempt e-mails. Some examples of recent ransomware attacks include:
Howard University Cancels Classes after Ransomware Attack
Hackers use Colonial pipeline ransomware news for phishing attack
The transition to Microsoft account management for all UM System campuses has given the S&T IT Security team the opportunity to use phishing email simulations. The simulations generate a fake email message that can be sent to any number of individuals and that recipients should interpret as a phishing email. The simulator can also monitor the email to see how the recipients respond.
The S&T IT department staff have already been through several simulations to see how well the IT staff are at identifying a phishing attempt. In the coming months, S&T IT will expand these simulations to the entire campus. We hope that the mandated cybersecurity training that must be completed by all staff and faculty by September 17 will prove beneficial and help our campus to respond appropriately to the simulations.
If you suspect that an email is a phishing attempt, please report it by:
- creating an email to S&T IT Security at security@mst.edu and attaching the suspicious email.
- selecting the Report Message icon in the message ribbon of the email to report the message to Microsoft.
Visit the Report Phishing Emails page for complete instructions.
Can You Guess?

The Rise in Ransomware Attacks Across College and University Campuses
In June of 2020, hackers seized network files from the University of California at San Francisco’s School of Medicine computer system. What followed was a negotiation between USCF and the cybercriminals who launched the attack that eventually cost the university $1.14 million in Bitcoin. This is only one example of ransomware attacks targeted at institutions of higher education.
Since the advent of Covid-19 and the switch to remote education, attempts to extract ransom by locking up college computer networks have doubled, costing colleges and universities that have been victims of successful attacks an average of $447,000. In June of 2021, colleges were the most targeted types of institutions by cybercriminals. They experienced more than six million malware attacks as opposed to businesses, which were targeted 900,000 times.
The Chronicle of Higher Education describes the rise in ransomware attacks on colleges and universities and reviews the strategies institutions have been using to thwart those attacks in its Trends Snapshot article, Defending College Computer Networks. Read the complete article for more information.
IT by the Numbers
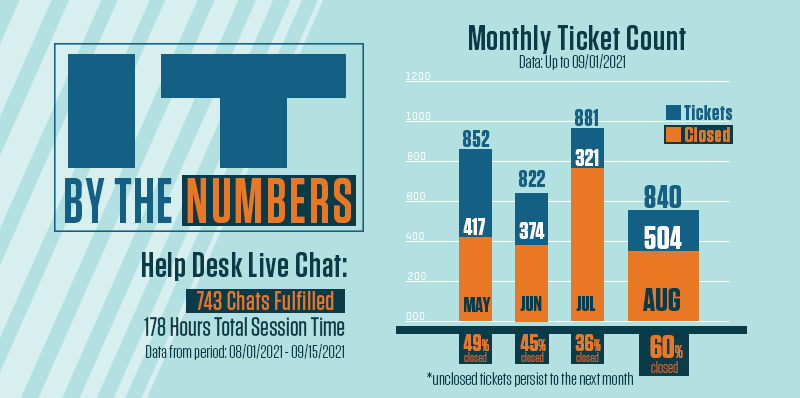
The IT by the Numbers graphs and statistics are added to our new IT Support Stats webpage. Check it out!
Remembering Richard Altheide (March 5, 1961 ~ July 17, 2021)
by: Peggy Wilson
Richard Altheide spent his entire 37-year career here at UMR/S&T. He was instrumental in designing and building the network infrastructure and telecom system that is in use on campus today. He wrote the policies and procedures; created new techniques; educated students; and mentored several engineers.
When I started in IT way back in 2004, Richard Altheide was a bit of an anomaly. He was intimidating and scary smart. I was afraid to ask questions, but since I didn’t have a clue how to create a phone system on the network on my own, I had to ask Richard a LOT of questions. He took my inexperience in stride and calmly walked me through the processes. He was always there when I needed answers. My fear evaporated and a friendship blossomed. Richard had always been my mentor throughout my career, and frankly, I would not be where I am today if it weren’t for Richard.
His legacy is the network. It was his ‘child’. He developed it, nurtured it, and helped it grow into the stable network infrastructure that the entire campus community relies on today. He mentored all the network engineers and helped them become experts in the field. Richard was a highly respected member of the campus community and was frequently sought out to assist other groups in IT. “Ask Richard” was a familiar expression here in IT because everyone knew if anyone would have the answer, it would be Richard.
I will miss my teacher, my Yoda, my colleague, my friend.

Data Clasifications and What They Mean for You
Data is everywhere. We deal with it every day. It comes in all shapes and sizes, from the post-it note on the side of our computer monitors; student records in PeopleSoft; an email from a manager – to the complex data set we use for our research. It is important to realize that the data we deal with on a daily basis can be classified by it’s content and the audience it can be shared with. It is important to understand these classifications when deciding where to store the data and who it is shared with.
S&T IT uses the Data Classification System as defined by UM System to determine how to classify data. There are four levels of classifications: Public, Sensitive, Restricted, and Highly Restricted.

The first level, DCL1 (Public), is data that is created for the public. Information in the eConnection or on the IT website is public data and does not harm anyone or anything associated with it. You can store DCL1 data anywhere and share it with anyone because it is intended for a public audience.
The second level, DCL2 (Sensitive), is data that is not public, and could be considered harmful if it was disclosed. There is no policy on the disclosure of DCL2 information. For example, there is no policy against release of staff home phone numbers, but people would be very unhappy to find such a list available online. DCL2 data can be stored anywhere that is not publicly accessible, for example in cloud storage or saved on your computers. You can share DCL2 data in email.
The third level, DCL3 (Restricted), is data where disclosure is restricted by regulations and policies. For example, FERPA protected data is DCL3 data, and accidental disclosure of this information can have very serious consequences for you and the University. DCL3 data can be stored on campus network storage, which you will hear referred to as the S&T S: and Y: drives. IT Security recommends against storing DCL3 data on campus computers, and discourages storing DCL3 on a laptop or unencrypted USB drive. Laptops and unencrypted USB drives can easily get lost or stolen, and control of what happens to the data stored on them is also lost.
The fourth level, DCL4 (Highly Restricted) data, like DCL3 data, is also restricted by regulations and policies that define unauthorized disclosure. Disclosing DCL4 data results in more severe consequences. An example of DCL4 data is Controlled Unclassified Information (CUI). CUI pertains to data that is a part of government funded research, and in the future will also include student financial aid information. You should only store DCL4 data on approved cloud storage, or on encrypted hard drives. IT Security recommends using Microsoft Teams or an encrypted email through Outlook 365 online to share the data.
It is important to note that you can store and share DCL3, DCL2, and DCL1 data on any storage or sharing method approved for DCL4. When in doubt, use DCL4 approved storage and sharing methods for any data. However, if you do use the same storage method for different data classification levels, make sure not to combine them. Do not put DCL1 and DCL 4 data in the same folders. Put them in different folders to avoid accidentally sharing the more restrictive data.

If you have further questions about your data’s classification level or how to safely store and share it, feel free to contact IT Security at security@mst.edu.
Answer to Can You Guess?
The answer is B. There are 1283 VOIP phones on the S&T campus.

